It's crucial that you protect your small and medium-sized farming enterprises (SMEs) against cyber incidents as you embrace technology in all areas of operations, including email, text, online banking, and smart farming tools. Precision agriculture and automation can boost efficiency and productivity, but they also bring new cyber risks. Without robust safeguards, cyber threats can disrupt your operations, impact your profits and damage the trust you've built with your customers. Staying ahead of these cyber risks will help your farm thrive in the digital age.
On this page
- Report a cyber incident
- Learn about cyber security and cyber incidents
- Protect your farming business from cyber incidents
- Access more cyber security information
- Cyber security toolkit
Report a cyber incident
If you believe you or your farming business was a victim of a cyber incident, please report it immediately to the Canadian Centre of Cyber Security. Your business details will remain confidential. Your reporting helps you:
- access expert assistance
- identify threats and prevent future attacks
- contribute to a stronger defense network
- protect the entire agriculture and agri-food industry from similar threats
While we can't guarantee that you'll be protected from all forms of cyber incidents, you can take steps to safeguard your agribusiness from cyber risks and significantly increase the protections you have from the most common cyber incidents.
Learn about cyber security and cyber incidents
What cyber security is
The protection of digital information, and the systems that store and send it, involves using various technologies, processes, and practices to keep networks, computers, programs, and data safe from attacks, damage, or unauthorized access. This ensures that the information remains private, accurate, and available when needed.
The main purpose of cyber security is to protect your devices (cellphones, laptops, computers, etc.), the data they hold, and the services you use (both personal and corporate). Cyber security measures can flag suspicious downloads and spam emails, ensure that only authorized people have access to your systems, and encrypt sensitive information. More importantly, cyber security safeguards the valuable data that these devices and systems hold, such as feed rations, medications for animals, crop outputs and trends, and customer/client information.
Examples of cyber incidents that affect the agriculture and agri-food industry
-
Phishing emails that try to steal your personal data or gain access to your business systems
Phishing emails are deceptive messages designed to trick you into revealing personal information, such as passwords or credit card numbers. These emails often look legitimate, resembling communications from trusted organizations like banks or online services, and may contain urgent requests to prompt immediate action. Organizations are particularly at risk because employees can open these emails on workstations, potentially compromising the entire network.
-
Fraudulent texts and calls
Fraudulent calls and texts are scams designed to deceive you into providing personal information or money. These messages often appear genuine, resembling communications from banks or government agencies, and may use urgent language to prompt a quick response. Always verify the source before responding to any unsolicited communication.
-
Ransomware demands
Ransomware demands are malicious messages that appear after your computer or files have been encrypted by ransomware. These demands typically inform you that your data is locked, and you must pay a ransom to regain access. They often come with detailed instructions on how to make the payment, usually in cryptocurrency.
-
Network breaches that steal your sensitive data
Network breaches that extract and steal your sensitive data are serious cyberattacks where hackers gain unauthorized access to your network and steal confidential information. These attacks can happen through weak passwords, phishing emails, or outdated software. For you, this might look like unexpected changes in your accounts, unfamiliar transactions, or unusual network activity.
For more information on phishing and other common cyber threats, read Get Cyber Safe Guide for Small Businesses.
Anyone can be a target
A cyber incident isn't personal. Anyone, individuals and organizations alike, can be targeted. Many cyber incidents, such as phishing, require little effort and minimal resources from the attackers. Threat actors can easily and widely carry out these attacks, casting a broad net that can trap unsuspecting and inattentive victims.
The more difficult it is to hack a farm system, the more likely threat actors are to move on to another, easier, target. No one wants to be an easy target.
A cyber incident can have a lasting impact on you and your farming business
If you experience a cyber incident it can be challenging, but if you understand the potential lasting impacts then you can take the right steps toward recovery and future prevention. Even if you deal with an immediate issue, such as paying ransomware, there are other aspects to consider. These could include:
Operational disruption
Cyber incidents can severely disrupt the operations of agriculture and agri-food SMEs. For example, ransomware attacks can lock critical systems and data, halting production, distribution, and supply chain activities. Such disruptions can lead to delays in delivering products to market, spoilage of perishable goods, and loss of trust among your business partners and customers. The recovery process from these disruptions can be time-consuming and costly, further affecting business continuity.
Reputational damage
Reputation is crucial in the agriculture and agri-food sector, where trust and reliability are key to business success. Cyber incidents can erode customer trust if sensitive data, such as customer information or trade secrets, is compromised. Negative publicity resulting from a data breach or cyber incident can damage your brand and reduce its competitive advantage. This reputational harm can have long-lasting effects, making it difficult to regain the confidence of customers, suppliers, and investors.
Legal and regulatory consequences
Agriculture and agri-food SMEs are subject to various regulations and standards concerning data protection and food safety. A cyber incident that leads to a data breach or compromises food safety protocols can result in legal action, fines, and penalties from regulatory bodies. Additionally, you may face lawsuits from affected parties, further straining your financial and operational resources. Compliance with post-incident regulatory requirements can also be burdensome and require significant effort and investment.
Supply chain and business ecosystem impact
Cyber incidents on agriculture and agri-food SMEs can have cascading effects on the wider supply chain. Disruptions in one part of the supply chain can impact suppliers, distributors, and retailers, causing broader economic repercussions. The interconnected nature of the agri-food sector means that a cyber incident affecting one company can have ripple effects, highlighting the need for robust cyber security measures across the entire supply chain.
Agriculture systems are at risk of a cyber incident
Targets can include:
- production, financial, customer and other data
- wireless sensors
- automated and robotic machinery
- autonomous and semi-autonomous vehicles and equipment
- heating, refrigeration, lighting and ventilation controls and systems
Protect your farming business from cyber incidents
No farming operation, regardless of size, is immune to cyber incidents. SMEs often believe they are too small to be targeted. However, this misconception can lead to a lack of preparedness and make them easy targets for cyberthreat actors.
There are effective solutions and strategies to improve your preparedness.
Use strong passwords
- Use different passwords for your email, banking and other accounts
- preferably 12 characters-long
- include 1 uppercase letter and 1 lowercase letter
- include 1 special character
- Change your passwords frequently (every 3 months)
- Don't write your passwords down on paper or save copies of your passwords on your phone and password manager
Prevent phishing attacks
Don't open emails if the sender is unknown to you and don't click on links or attachments in emails unless you're sure of their origin and legitimacy. Look for the 7 red flags of phishing (Get Cyber Safe) in emails or texts you receive to help spot a phishing attack.
Take cyber security training
Ensure your employees are cyber aware and on alert for threats like scams and phishing attempts. The Government of Canada offers an online self-paced course about Cyber Security for Small and Medium Organizations for SME owners. The course:
- is free of charge
- has topic-based modules ranging from 20-60 minutes in length to complete
The modules can be taken as stand-alone lessons or combined in any order, depending on your interests.
Other important tips
- Take the 10-question Get Cyber Safe self-assessment to help assess the security of your business accounts.
- Develop an incident response plan for your business. It enables a swift and effective reaction to cyber incidents, minimizing damage and downtime.
- Safeguard your data. Don't save personal or financial data on browsers if prompted, avoid auto-fill features.
- Don't use public Wi-Fi to access your on-farm digital systems. Instead of using public Wi-Fi, purchase and use a VPN (virtual private network) service for mobile devices.
- Protect your accounts. Enable multi-factor authentication on all your accounts, wherever possible.
- Back up and store vital information regularly, offline or in an external drive, including vendor and client data and information.
- Make sure your systems are always up to date. It ensures the latest security patches are applied, protecting against vulnerabilities and cyber threats.
- Reach out to your IT service providers and sector associations. Get technical help and stay informed about new threats and how to manage them.
- Be preventive. Install verified anti-virus/anti-malware software.
Access more cyber security information
- Canadian Centre for Cyber Security
- The Canadian Cyber Security Self-Assessment Tool
- Get Cyber Safe
- CyberSecure Canada: Certification program
- Boost Your Business Technology Grant
- Why cyber security is important - Video (Farm Credit Canada)
- Taking your farm data to the digital cloud (Farm Credit Canada)
Cyber Security Toolkit
The Cyber Security Toolkit is designed for small and medium-sized farming and agri-food businesses who are looking for practical resources and easy-to-implement best practices to help with cyber security preparedness.
Download the Cyber Security Toolkit (PDF, 697 KB)
What's inside the Toolkit
Cyber security risks and resources: Safeguarding Canadian agriculture and agri-food
As agricultural and agri-food businesses become more digitized and connected online, the need to safeguard against cybercrime increases. Precision agriculture, automation and smart farming technologies contribute to efficiency and productivity, but without proper safeguards, the door opens to cyber vulnerabilities that can range from disruptive to devastating effects, including paralyzing business and impacting profitability and consumer trust.
In this digital landscape, it's critical to understand and guard against cyber risks.
What cyber security is
Cyber security is the practice of safeguarding computer systems, networks and data from digital disruptions. Examples of cyber incidents affecting the agriculture and agri-food industry include fraudulent texts, phishing emails that seek to gain private info and access to systems, and ransomware demands, to name just a few.
At risk agricultural systems
Targets can include production, financial, customer and other data, wireless sensors, automated and robotic machinery, autonomous and semi-autonomous vehicles and equipment, and heating, refrigeration, lighting and ventilation controls and systems.
Quick tips to minimize your risk
- Have different passwords for each account, preferably 12 characters-long, including 1 upper and 1 lower case letter, and 1 special character. Change passwords frequently.
- Enable multi-factor authentication on all your accounts, wherever possible.
- Back up vital information regularly, including vendor and client data and information. Store backup information offline or in an external drive.
- Don't open unknown emails, and don't click on links or attachments unless you're sure of their origin and legitimacy.
- Don't save personal or financial data on browsers if prompted and avoid auto-fill features.
Get started today with these tools and resources
Canadian Centre for Cyber Security
A go-to resource for expert advice, guidance, services and support, and to report cyber incidents
Public Safety Canada
Access the Canadian cyber security tool assessments.
Community Safety Knowledge Alliance
Access targeted resources to help protect your farming business
Cyber Security Checklist
Simple steps you can take today to improve your cyber security and help keep you and your business protected.
Secure your devices and data
-
- This includes the passwords of the routers for Wi-Fi network(s) and tractors and other machinery in the field.
-
- Employees are reminded to change their passwords every quarter and they cannot reuse a password.
-
- MFA adds an extra layer of security to accounts and makes it harder for threat actors to gain access.
Stay updated, stay safe
-
- Periodically checking app permissions ensures they don't access data that is not relevant to their function.
- Turn off the permission that allows an app to know your location when you are not using it.
-
- This includes key contact information on clients, vendors, partners, and any proprietary agricultural data collected from agriculture technology devices on your farm
For more information on how to minimize your cyber security risks, visit Get Cyber Safe.
Questions to ask before you make your next AgTech purchase
As your farming business becomes more digitized and connected online, it's critical to guard against cyber security risks. These questions can help guide your conversation with agriculture technology vendors so you can make informed decisions about who you trust to protect your business from cyber security risks and safeguard your data and operations.
- Does the vendor have a good reputation?
- How long has the vendor been in business?
- Is the vendor known to you?
- Does the vendor work with other companies in your sector?
- Do they know your line of business or commodity?
- Are they expanding their reach in your sector, or are they new to your sector?
- Do the companies have a good reputation?
- Will the vendor provide contact information for customers you can speak to for feedback (known as reference customers)?
- Can the vendor explain your contract in plain language?
- Can they explain the clauses in your contract in a way that's easy to understand?
- Can they tell you where your information is stored, who has access, and how it is protected?
- What steps will the vendor take if there is a data breach that impacts data they have stored about you and your business?
- Have there been previous data breaches? If so, what happened?
- Can they explain simply how your data is stored and protected?
- Do they have an emergency response plan they can share with you?
This isn't a full list of questions, but it's a good starting point for talking with a new vendor.
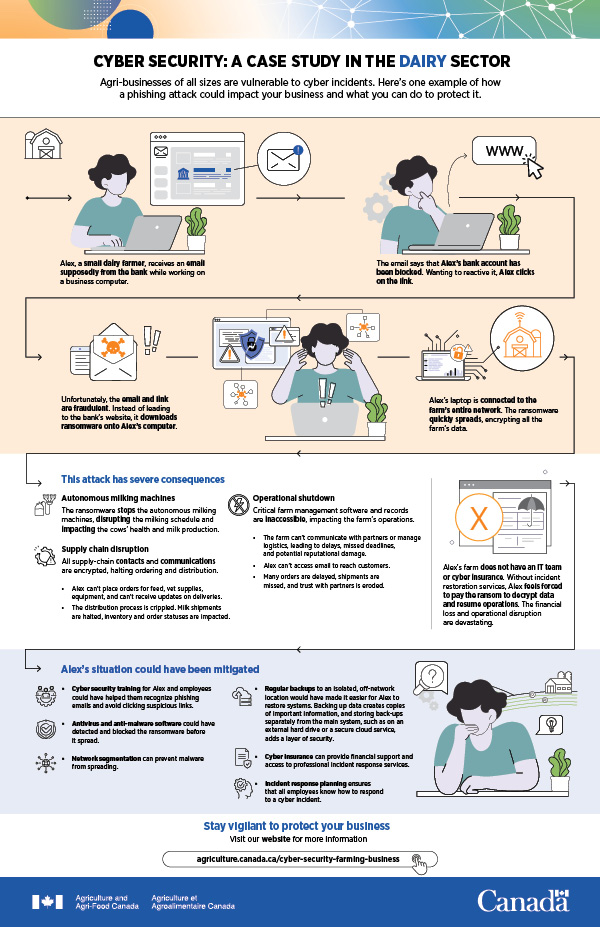
Cyber security: A case study in the dairy sector
Agri-businesses of all sizes are vulnerable to cyber incidents. Here's one example of how a phishing attack could impact your business and what you can do to protect it.
Alex, a small dairy farmer, receives an email supposedly from the bank while working on a business computer.
The email says that Alex's bank account has been blocked. Wanting to reactive it, Alex clicks on the link.
Unfortunately, the email and link are fraudulent. Instead of leading to the bank's website, it downloads ransomware onto Alex's computer.
Alex's laptop is connected to the farm's entire network. The ransomware quickly spreads, encrypting all the farm's data.
This attack has severe consequences
Autonomous milking machines
The ransomware stops the autonomous milking machines, disrupting the milking schedule and impacting the cows' health and milk production.
Supply chain disruption
All supply-chain contacts and communications are encrypted, halting ordering and distribution.
- Alex can't place orders for feed, vet supplies, equipment, and can't receive updates on deliveries.
- The distribution process is crippled. Milk shipments are halted, inventory and order statuses are impacted.
Operational shutdown
Critical farm management software and records are inaccessible, impacting the farm's operations.
- The farm can't communicate with partners or manage logistics, leading to delays, missed deadlines, and potential reputational damage.
- Alex can't access email to reach customers.
- Many orders are delayed, shipments are missed, and trust with partners is eroded.
Alex's farm does not have an IT team or cyber insurance. Without incident restoration services, Alex feels forced to pay the ransom to decrypt data and resume operations. The financial loss and operational disruption are devastating.
Alex's situation could have been mitigated
- Cyber security training for Alex and employees could have helped them recognize phishing emails and avoid clicking suspicious links.
- Antivirus and anti-malware software could have detected and blocked the ransomware before it spread.
- Network segmentation can prevent malware from spreading.
- Regular backups to an isolated, off-network location would have made it easier for Alex to restore systems. Backing up data creates copies of important information, and storing back-ups separately from the main system, such as on an external hard drive or a secure cloud service, adds a layer of security.
- Cyber insurance can provide financial support and access to professional incident response services.
- Incident response planning ensures that all employees know how to respond to a cyber incident.
Stay vigilant to protect your business
Cyber Security Glossary
- Anti-virus/anti-malware software
- A program used to prevent, identify, and remove viruses and other malicious software from your computer.
- Business continuity
- An organization's ability to continue with essential functions during a disruption, such as a cyber incident or natural disaster. A business continuity plan or BCP outlines the protocol and processes an organization follows to ensure that operations continue with as little disruption as possible.
- Cyber incident
- Attempt by threat actors to cause harm, destroy, or gain unauthorized access to sensitive information in a networked computerized system.
- Cyber safeguards
- Measures taken to protect data, networks and computer systems from unauthorized access, theft, or damage.
- Downtime
- Not being able to access a system due to the failure of the system, application, or the entire network of a company. Downtime can occur due to maintenance activities, power cuts, or unexpected technical failures from cyber incidents. Consequences can include loss of revenue, decreased productivity, costs to recover systems and reputational damage.
- External drive
- A storage device that connects to your computer, often via USB (Universal Serial Bus), FireWire or Thunderbolt connection.
- Incident Response Plan
- A written document, formally approved by the senior leadership team, which helps your organization before, during and after a confirmed or suspected cyber security incident.
- Internet of Things (IoT)
- A network of physical devices that transfer data to one another without human intervention. IoT are not limited to computers and can include anything with a sensor, software, and network connection.
- Malware
- Abbreviation for 'malicious software'. Malware is designed to disrupt or harm computer systems.
- Multi-factor authentication (MFA)
- The use of two or more authentication methods to log into a system. For example, you are required to enter a code from an authenticator app after entering your password to log in. MFA prevents threat actors from gaining access with just one exploited password.
- Network breach
- When a threat actor finds a way to bypass your security to get inside your network. Once they have access to the system, they can gain unauthorized access to data, applications, and devices.
- Phishing
- A form of fraud that involves contacting victims through email, telephone, or text to trick them into sharing personal information. Phishing scams often aim to persuade victims to transfer money, reveal financial information, or share system credentials such as passwords.
- Ransomware
- A type of malicious software designed to block access to a computer system until a sum of money is paid.
- Security patch
- A software update that helps address vulnerabilities, bugs and resolves inconsistencies in a software.
- Spam
- Unsolicited communication sent in bulk. Spam can be sent via email, phone, text messages (SMS) and social media.
- Threat actor(s)
- An individual or group who tries to access data they aren't authorized to access or cause harm to digital systems. Often referred to as a "hacker" or "cyber criminal".
- Virtual Private Network (VPN)
- An encrypted internet connection that aims to provide a secure, private network connection for safe data transmission to and from networked devices.
Feature

Dr. Janos Botschner from the Community Safety Knowledge Alliance and Christine Beauchamp from the Canadian Centre for Cyber Security tell us some true cyber heist stories